A "sane" wireguard server on an ASUS router
Posted Thu, 09 May 2024 21:29:00 +0100 | Networking|
I host a backup server at my parents place, and connect to it using a VPN into their network. They are using an ASUS ZenWifi AX router with stock firmware. Although being locked down, it supports a couple of different VPN options through its web interface. I have used OpenVPN with it a lot in the past, but I have taken a liking to wireguard due to its relative simplicity, and wireguard also happens to be supported by the router.
There is however one big problem. You cannot generate your own keys. The router generates a public and private key and expects you to use them, which means that ASUS would have the means to break the VPN encryption and also impersonate your wireguard peer should they desire. Whether this design choice is on purpose or due to ignorance I will leave to the conspiracy theorists to discuss.
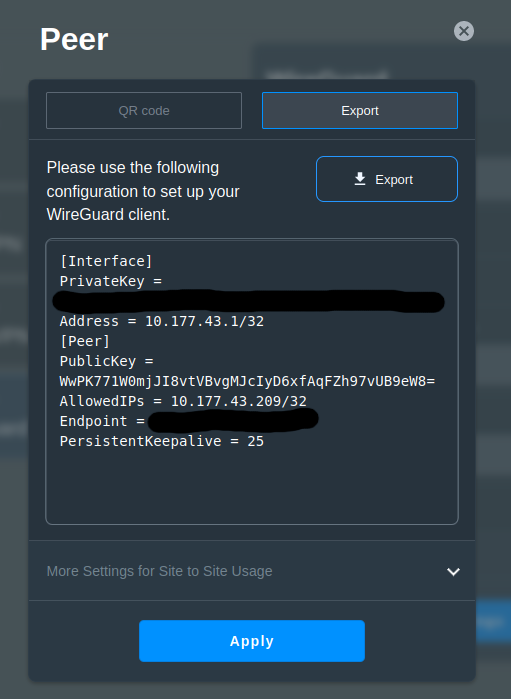
But in all seriousness, you could argue that this doesn’t really matter since the router would already see the unencypted traffic as it exists the router, and there are easier ways for ASUS to access your private network should they want to. Nevertheless, I still wanted to see if there was a way I could trick the router into using my own keys.
After sshing into the router, I started looking into the source code of the web interface under /www and found that the wireguard configuration
(and a bunch of other stuff) is modifiable using a nvram command. The public and private key used for the wireguard VPN are located under the
wgs1_c1_pub and wgs1_c1_priv keys, respectively, in the configuration viewable using nvram show. However, I quickly found
that modifying this configuration through nvram set has no useful effect.
Eventually, I found that the wg binary was installed on the router. I created a quick configuration file looking like this,
and placed it in /etc/wg/wgs1.conf in the router.
[Interface]
ListenPort = 12345
PrivateKey = longbase64stringhere
[Peer]
PublicKey = anotherlongbase64stringhere
AllowedIPs = 10.177.43.1/32, 10.0.39.0/24
Then I just ran wg setconf wgs1 /etc/wg/wgs1.conf, and from then on everything worked! wg show clearly showed the public key of my wireguard peer,
but the web interface still incorrectly showed that only the public key generated by ASUS was trusted.
Now, this method is not perfect, as whenever the router reboots the wireguard configuration is reset. As such, at the end of the day I am
still reliant on OpenVPN in case there is a blackout. Unfortunately the router doesn’t have crontab or anything I could use to refresh my
wireguard configuartion periodically. Will post an update if I get around to finding a more stable “sane” wireguard setup on the router.